20+ cyber security diagrams
11 What is a Data Flow Diagram Lucidchart. Cybersecurity Map 20.

Attack Tree Diagram B For The School Computer Network Download Scientific Diagram
Senior managers understand the.
. Network Security Diagram Template. 12 Creating Good PCI-DSS Network and. Training is planned to up-skill all staff students and visitors to optimise our front-line defences against cyber-attacks.
Creately diagrams can be exported and added to Word PPT powerpoint Excel Visio or any other document. The CIS 20 cybersecurity model is designed to be all-encompassing and require extreme attention and care to an organizations cybersecurity management process. Draw Network Diagram with Visual Paradigm Online VP Online a web-based Network Diagram maker.
However being a CISSP myself you can certainly see some of familiar. Without this information CISOs and security advisors cannot identify system. You can edit this template and create.
9 Data flow diagrams Cloudgov. The top 20 attacks sorted loosely from least to most sophisticated are. Cybersecurity classic Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple image formats.
Figure 3 shows the contest area which is composed of a cage for the cyber-physical security honeypot made from plastic orange construction fence in order to ensure the safety of DEF. These network infrastructure diagrams are essential to any cybersecurity program. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution.
10 Create a threat model using data-flow diagram elements Learn. 1 ics insider 2 it insider 3 common ransomware 4 targeted ransomware 5 zero-day ransomware 6 ukrainian. The map is not based on a particular standard or framework.
The Network Diagram editor has tailor-designed. Use PDF export for high. You can edit this template and create your own diagram.
Cyber security diagram 2018.
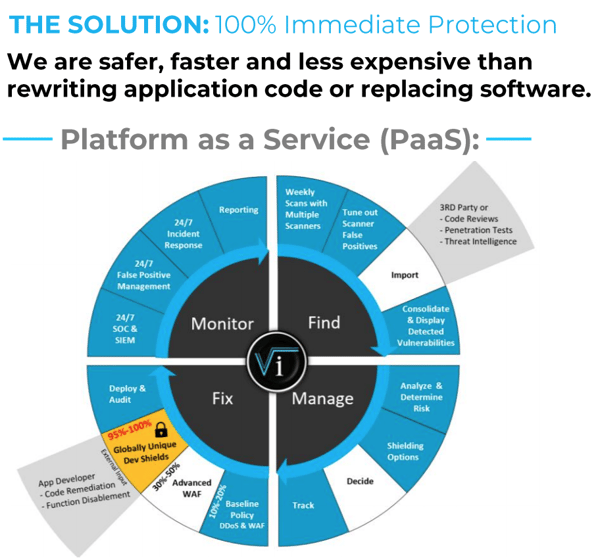
Managed Cyber Security Services

Top 10 Cyber Security Threats Amid Covid 19 Pandemic Download Scientific Diagram

Top 20 Countries With Cyber Crime 15 Iv Crimes On The Internet Download Scientific Diagram

Diagram Of Cyber Security Investment Decisions Inputs And Outputs Download Scientific Diagram

Illustration Of Cyber Security In Smart Grids Download Scientific Diagram

Typical Diagram Of A Three Phase Mg With Cyber Attack Download Scientific Diagram
The Schematic Diagram Of The Hybrid Cyber Attack Download Scientific Diagram
Top 10 Cyber Threats Pie Chart Download Scientific Diagram

Top 20 Countries Generating Cyber Crime 15 Download Scientific Diagram

Internal Security Incidents By Entry Point Download Scientific Diagram

Illustration Of Cyber Security In Smart Grids Download Scientific Diagram

Attack Tree Diagram A For The School Computer Network Download Scientific Diagram
15 646 Cybersecurity Photos Free Royalty Free Stock Photos From Dreamstime
The Cybersecurity Ontology Download Scientific Diagram
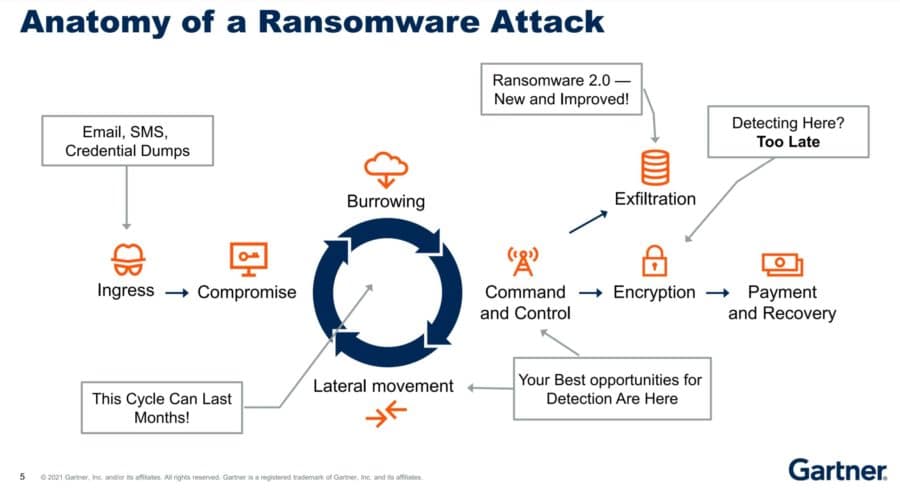
Cybersecurity Mesh And Decentralized Identity Explained

Structure Of Proposed Network Security Model Download Scientific Diagram
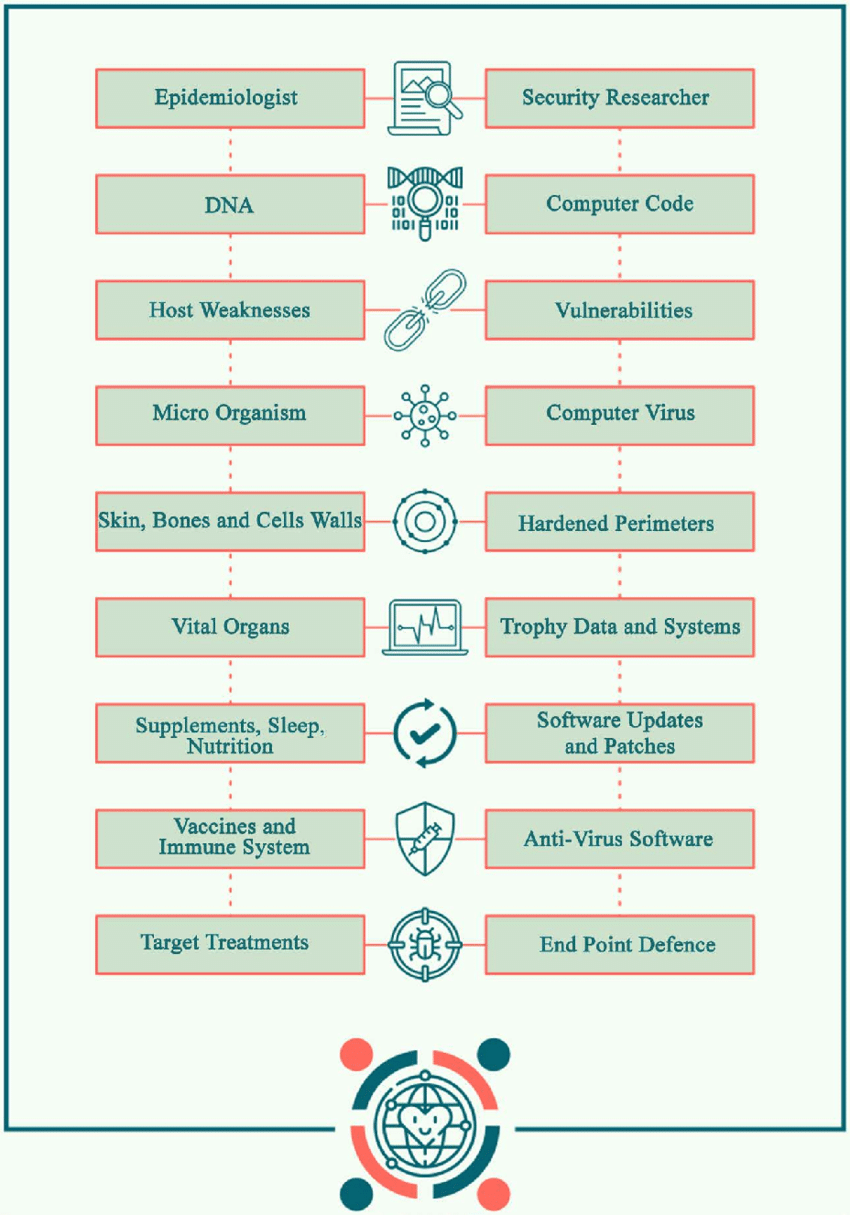
Schematic Diagram Comparing Epidemiological Principles To Cyber Download Scientific Diagram